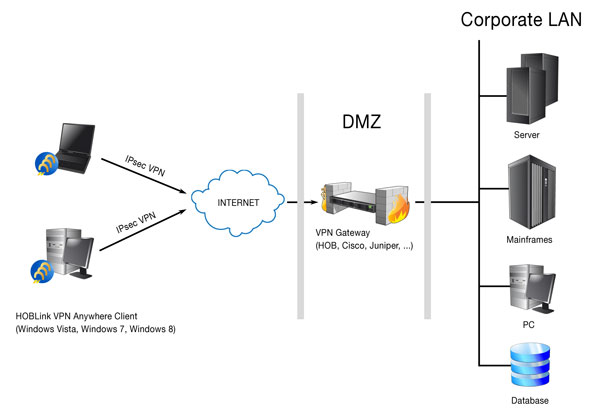
A new study to come out from the Sapienza University of Rome and Queen Mary College of London has identified that the lot of industrial virtual-private-network (VPN) providers utilize methods which can be available to attacks. The possibility is there, the investigators say, for those utilizing VPN providers to get their browsing history and other Internet-related traffic viewed by outside actors, without a lot of trouble.
 Of all 16 services regarded as part of the analysis, just one was shielded from DNS hijacking. Nevertheless actually that one fell down when it found IPv6-leakages, alongside 13 of the VPN businesses that are other.
Of all 16 services regarded as part of the analysis, just one was shielded from DNS hijacking. Nevertheless actually that one fell down when it found IPv6-leakages, alongside 13 of the VPN businesses that are other.
You just want to watch your blocked tv shows from abroad? Read more.
To make matters worse, the Stage was employed by over half the providers looked at -to-Point Tunnelling Method with MSCHAPv2 authentications, which makes them vulnerable to brute-force hacks.
These revelations are problematic for the sector — and particularly the businesses named and killed — as their whole task would be to obfuscate a user’s web traffic. If this is as obvious when when working with a VPN as without, then it is officially worse to use any of these solutions, since these expecting to infiltrate their servers are aware the man supporting the traffic doesn’t desire to be located.
Additionally, this is unhappy news for those that were hoping to conceal their traffic with a overintrusive government. While some VPN suppliers could be unlikely to work immediately with all the authorities of any country, the NSA and GHCQ have shown a penchant for coughing along with the use of malware (read more about vpns and malware here) to garner information, so that it wouldn’t be surprising to to find out that that many of these VPNs have been infiltrated by government businesses.
Are these VPN providers used by some of you? If so, can you want to keep on doing so after these facts? So how to change IP Address? What is secure right now?